The assumption that software security can stay ahead of the hackers is not true because the software security industry is always reacting to threats that hackers expose. Once hackers start exploiting a flaw in an application, security companies try to block the resulting threat by providing security updates for existing software or by developing new programs. Either...
Email is one of the most critical business tools and a major component of the lives of many people. At the same time, it seems to lack adequate security as the Clinton campaign email leaks and the publication of France’s Macron emails have shown. Email is at the same time insecure but used to share important and often sensitive information. While companies encrypt...
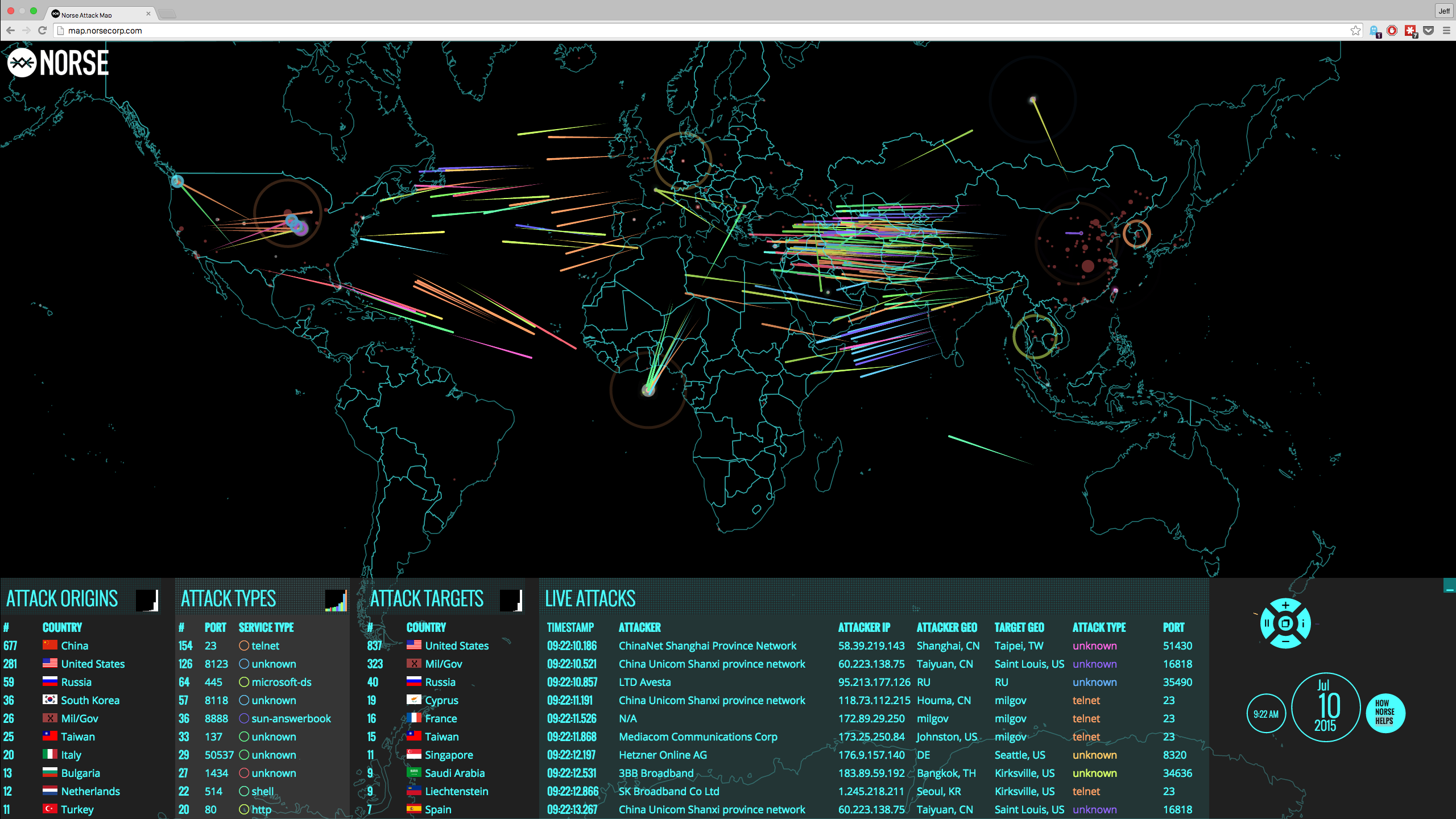
A lack situational awareness is hurting the ability of companies and the public sector to adequately protect sensitive information. Intellectual property, sensitive business data, personally identifiable information and infrastructure access, are at risk. Situational awareness in the context of cybersecurity involves the following three areas: Effective management of...
The storing and processing of data sets that contain personally identifiable information (PII) is increasingly regulated and is subject to onerous notification requirements when data breaches occur. Such data includes health information, financial data and legal records. When your business stores or processes this information and when it can be linked to a particular...
This article is the third in a series that discusses data breach threats and possible solutions. The first two articles, “What You Need to Know,” and “Threats and Consequences,” make it clear that businesses need to take action to reduce data breach risks. The current article presents encryption as a possible solution but details what type of encryption is needed to...
This article is the second of a series that explores data breach risks and issues related to regulatory compliance, associated costs and loss of reputation. In “Threats and Consequences” we look at the types of cyber threats and what the consequences might be for businesses that suffer data breaches. As described in the first article of the series, “What You Need to Know
This article is the first of a series that explores data breach issues, threats to data security, compliance with regulations and effective solutions to reduce the risk of data breaches. In "What You Need to Know” we define key terms and provide an overview of the data security problems businesses are facing. Data breaches are becoming more frequent while government...
Data manipulation could mean disaster for corporations, health care providers, national security agencies and individuals around the world. Businesses and consumers both invest time and money into securing private information, but too often, the focus is on preventing hackers from accessing data and therefore ensuring that sensitive information, trade secrets and...
Reports of data protection fails against insiders, compromised cybersecurity and data breaches are becoming more frequent, even at large corporations and the government. But these events are not all the same. You can analyze them and, by classifying the data breaches based on how they happened, you can develop effective countermeasures. One way data breaches occur is...
Effective cybersecurity is essential for law firm operations, for regulatory compliance and for keeping a good reputation, but it requires a familiarity with the principles of secure IT. Legal ethics require that lawyers keep private information secure and preserve client records. As a member of the legal profession, you have to ask how service providers deal with...