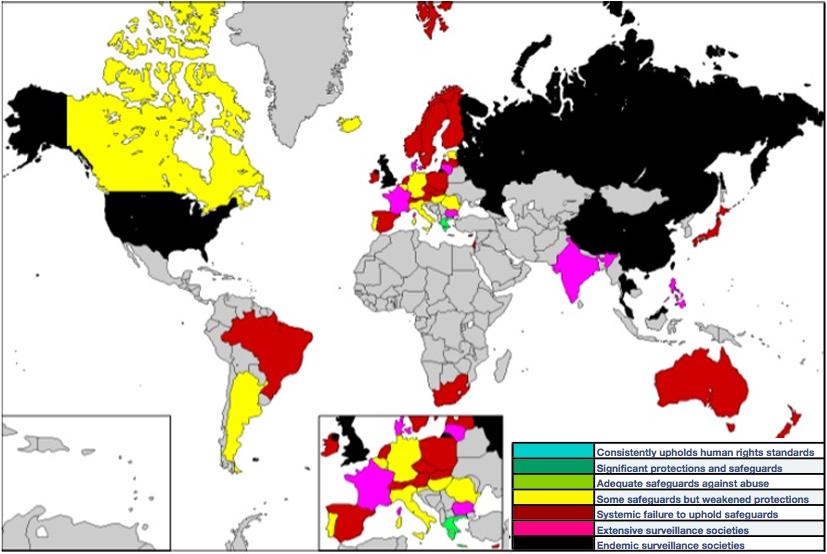
Cyberspace has no boundaries or borders, and this spells trouble for corporations around the world. Cyberspace has no boundaries or borders, and this spells trouble for corporations around the world. In an attempt to stamp out cyberespionage, governments are creating agreements dedicated to preventing cybercriminal activity and promoting better cyberawareness on both a...
October 25, 2015
Leave a comment
Breach,
Cybercrime,
Data Masking,
User Privacy,
Government surveillance,
data privacy,
cyber threats
By Wael Aggan
Without adequate email protection, some business people could experience personal and business-related disruption. The data breach of Avid Life Media demonstrated how easy it is for cybercriminal groups to steal incriminating information, as hackers successfully breached the company's network and made off with the personal records and account data of millions of...
August 27, 2015
Leave a comment
Email Security,
Personal Data Protection,
Breach,
data privacy
By Wael Aggan
Your data is valuable. Data security is not just a concern for corporations with millions of shoppers' payment card numbers and valuable intellectual property. As a consumer, you also need to implement data protection solutions if you want your personal emails, private information and sensitive data to stay out of the hands of cybercriminals, the government and data...
MITC attcks allow cybercriminals to access data and documents stored in popular file synchronization services such as Google Drive. Cloud storage has slowly but surely become the best method for sharing, backing up and remotely accessing data in all forms, from Word documents to movies to sensitive, personally identifiable information. So, given Google's position in...
Organized cybercrime is a major problem for today's businesses. Given the sophisticated nature of modern attack vectors and the value of personal data, it should come as no surprise that criminal organizations have formed with the intent of inspiring political change, committing corporate espionage and instilling their views on digital privacy on the world. In fact,...
If IRPs are mandatory to prepare for post-breach circumstances, organizations need to ask themselves these three questions. Data breach madness has reached a peak, as organizations slowly but surely discover one by one how no one is safe in today's cyberclimate. And experts universally agree that intrusions are inevitable, since attack vectors keep appearing in the form...
Many people feel that Cloud computing has been around for quite a long time, and intrusion into such technology is far from innovative. To them, it appears that instead of storing data on their own servers in a server farm, they now store their data in much larger clusters of servers in someone’s data center. The Cloud's threats arise from the sheer scale of data that...
This is the third part of 5 parts discussion where I will present the main risks of Cloud Computing and how CloudMask addresses those risks. I hope to receive your comments. W.A. Governments around the world have Digital Surveillance Programs that can be used to demand legal access to your data stored with a Cloud Service Provider (CSP) or Telecommunication companies....
Law firms need to balance compliance with the cloud in an age when both are critical to success. The cloud has become a fundamental part of business, and thanks to the cost-efficiency, scalability, and agility that these systems and services offer, it won't be going away anytime soon. From storage to computing, every organization in a variety of sectors has empowered...
October 21, 2014
Leave a comment
Data Sovereignty,
Compliance,
Breach,
Legal,
Data Masking
By CloudMask Team