A lack situational awareness is hurting the ability of companies and the public sector to adequately protect sensitive information. Intellectual property, sensitive business data, personally identifiable information and infrastructure access, are at risk. Situational awareness in the context of cybersecurity involves the following three areas:
- Effective management of data networks, IT assets and system configurations
- Awareness of threats including the tracking of incidents, the identification of internal suspicious behaviors and the knowledge of how external threats operate
- Awareness of the organization mission, the critical dependencies of IT operations and how specific failures affect organization operations
Most organizations have some aspects of situational awareness covered, but many don’t take a comprehensive approach that allows them to address data security in the face of new and sophisticated threats. They don’t have a clear and objective assessment of their data security policies and react to security incidents with a “more of the same” status quo protect my perimeter approach.
As a result, they construct a better, more impenetrable perimeter and implement additional login procedures such as two-factor authentication, hoping to create more protection for their data. But does two-factor authentication provide the required data protection relevant for today’s threats awareness?
Two-Factor Authentication
Authentication procedures are perimeter security processes that limit access to the data and do not protect the data itself. If you want to increase access security, you might opt for two-factor authentication. Authentication can be based on what you know, what you have and what you are. For example, a password is something you know, a mobile phone or a security token is something you have, and a fingerprint is something you are. Two-factor authentication uses elements from two of these authentication classes to increase security. Usually, the content of one of the elements changes with each use.
For instance, a user might have a password and, when he logs in, a unique code is sent to his mobile phone. He has to enter the code to complete his authentication. This process increases security against old-style hacking that uses a stolen database of usernames and passwords, but this is where situational awareness comes in. Two-factor authentication does not protect you in today’s situation where attacks are more sophisticated, or when the threats are coming from your cloud service providers, the vendors that you authorized to access your applications and government surveillance.
“Two-factor authentication isn't our savior. It won't defend against phishing. It's not going to prevent identity theft. It's not going to secure online accounts from fraudulent transactions.” Bruce Schneier
One type of attack common today is phishing, defined by the Anti-Phishing Working Group (APWG) as a “...mechanism employing both social engineering and technical subterfuge to steal consumers’ identity data...” Consumers clicking on links in fake emails are taken to counterfeit websites where they log in, disclosing their credentials to the hackers. Phishing attacks are increasing rapidly and, for the fourth quarter of 2016, APWG reported 1,220,523 phishing attacks, a 65% increase from 2015.
Such phishing attacks combined with man-in-the-middle hacking can completely defeat two-factor authentication. For example, a phishing email entices a consumer to click on a link to a fake website to verify his password. The consumer enters his username and password which the hacker sees and enters on the real website. The consumer has two-factor authentication enabled, and so the real website sends a code to the consumer’s mobile phone. The consumer enters the code on the fake website and the hacker, in turn, enters it on the real one. The consumer is shown a screen thanking him for verifying his password and does not realize he has been hacked. The hacker has access to the consumer account and can carry out transactions and change the security settings.
Vendors advocate for two-factor authentication as secure, but an independent situational analysis would show that attacks such as detailed above can penetrate such security.
Today’s Threats
Data is subject to threats from both outsides and inside the organization perimeter. While reliance on credentials such as username and password combinations or two-factor authentication are effective in reducing unauthorized access to the resources (e.g. network, segment, application), they are not immune to security failures. Theft of credentials and phishing emails linking to fake websites can defeat such strategies.
For internal threats, e.g. insiders with privileged access such as administrators and cloud service providers, are already inside the perimeter and they can access sensitive information beyond the established user authorizations. At the same time, government agencies can access the same information through blind subpoenas to the cloud providers and the use other techniques.
We must address the above scenarios. Data needs an extra layer of protection when credentials-based authentication and perimeter security fail or when insiders try to access private data.
Rather than doing more of the same with increasingly complex perimeter and login security measures, a data-centric approach identifies sensitive data and masks it so it can’t be read. When perimeter security fails, and login credentials are compromised, data-centric security keeps data safe because unauthorized individuals will not be able to read it.
Dynamic Data Masking (DDM) Protects Your Data
Perimeter security and login procedures limit access to data rather than protecting the data. If this access is compromised, through hacking or credential theft, your data is vulnerable. You may even have compromised secure access yourself by agreeing to give access to your emails or your data to various apps or social media sites. You need an additional security layer just for your sensitive data.
By utilizing DDM, Data is Masked as you generate it on your end device. As you type, the application changes individual characters to mask sensitive information while the physical structure of the data remains unchanged. This technique is easy to implement, and with the data structure unchanged, business processes such as SaaS, MS 365 and Google Apps can continue to function as before.
For instant; with CloudMask patent DDM, sensitive data is illegible for unauthorized individuals. When hackers gain access to your data, the masked text is useless. The application provides end-to-end data security independent of other security measures. When you authorize someone to see your data, it remains masked until the authorized person reads it on his computer or mobile device. The additional layer of security provided by CloudMask gives you complete control of your data and keeps it safe.
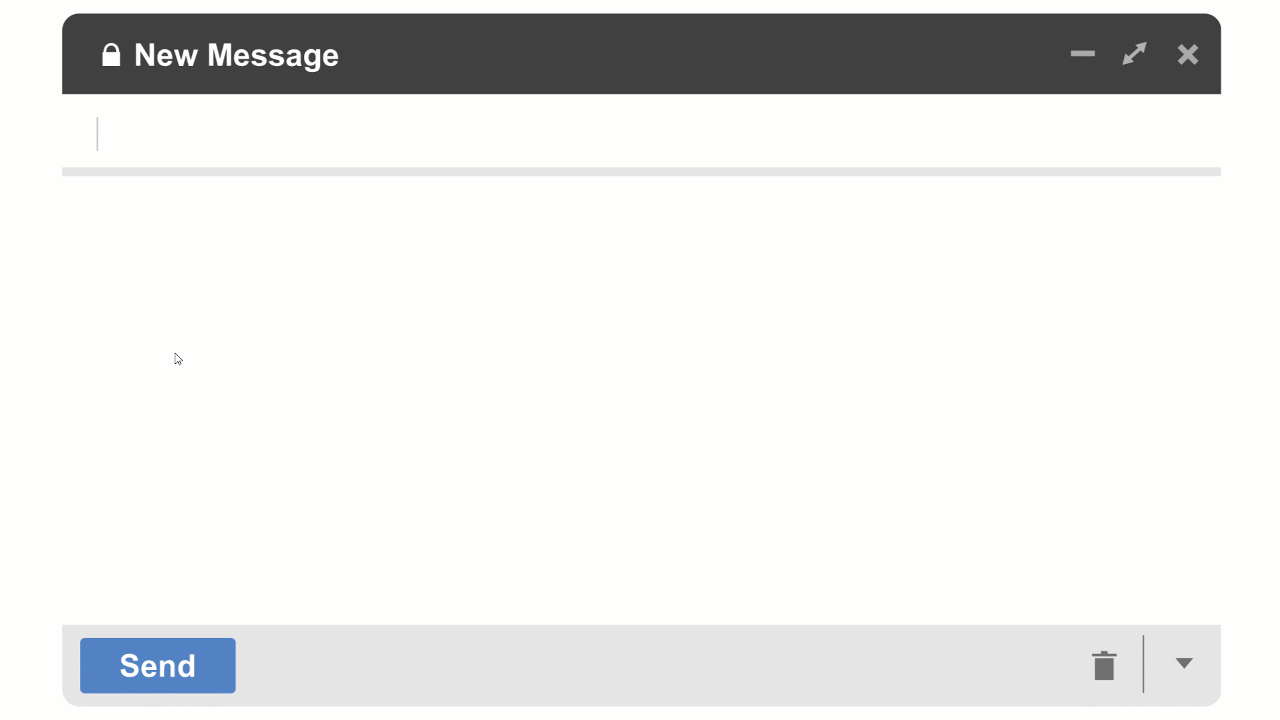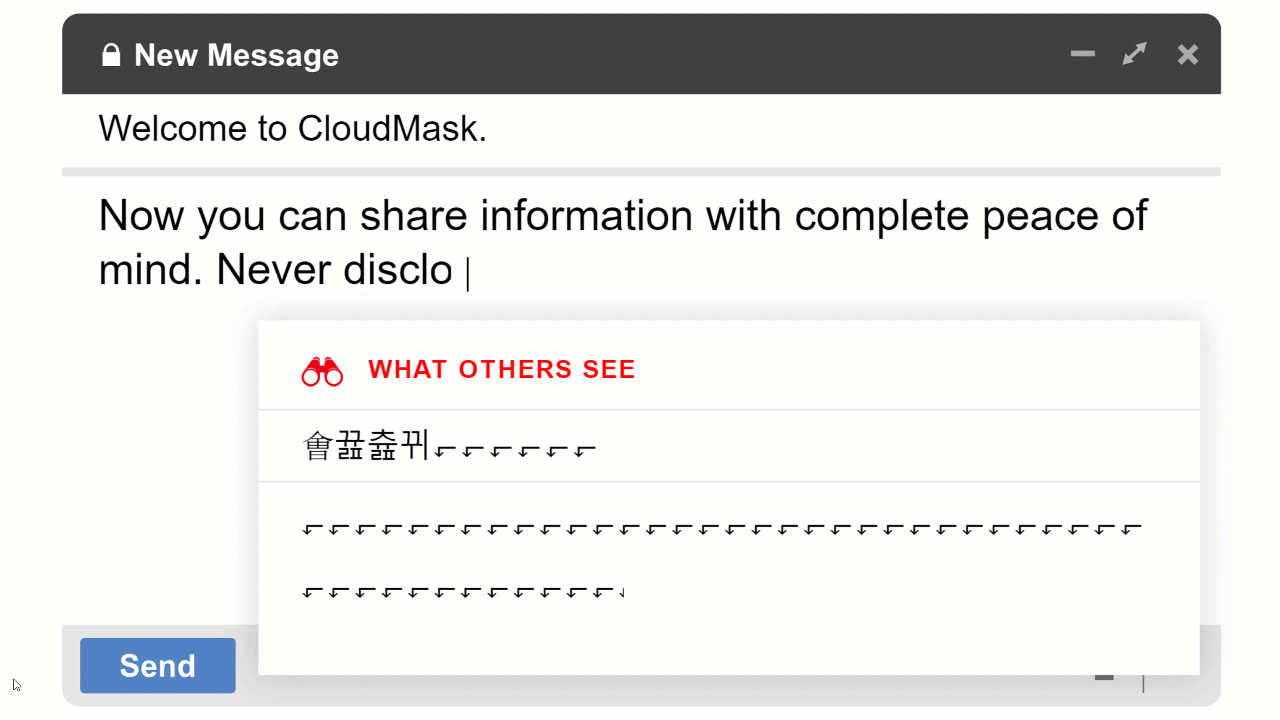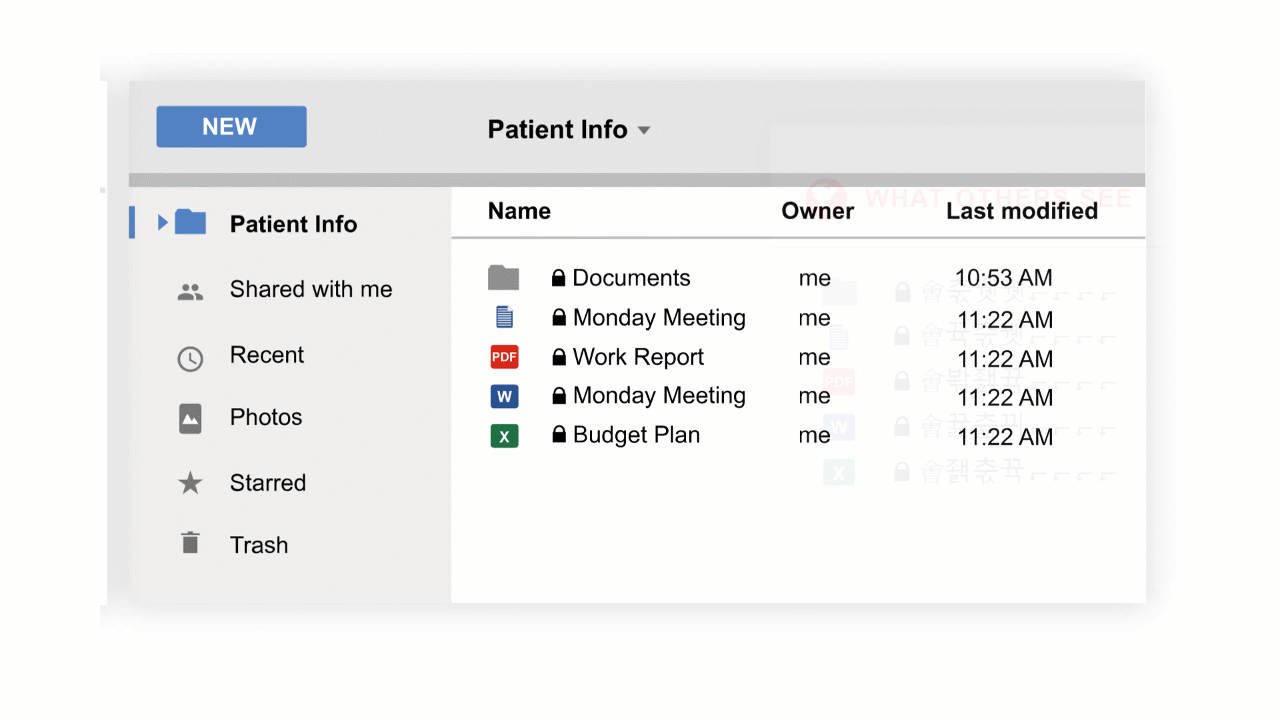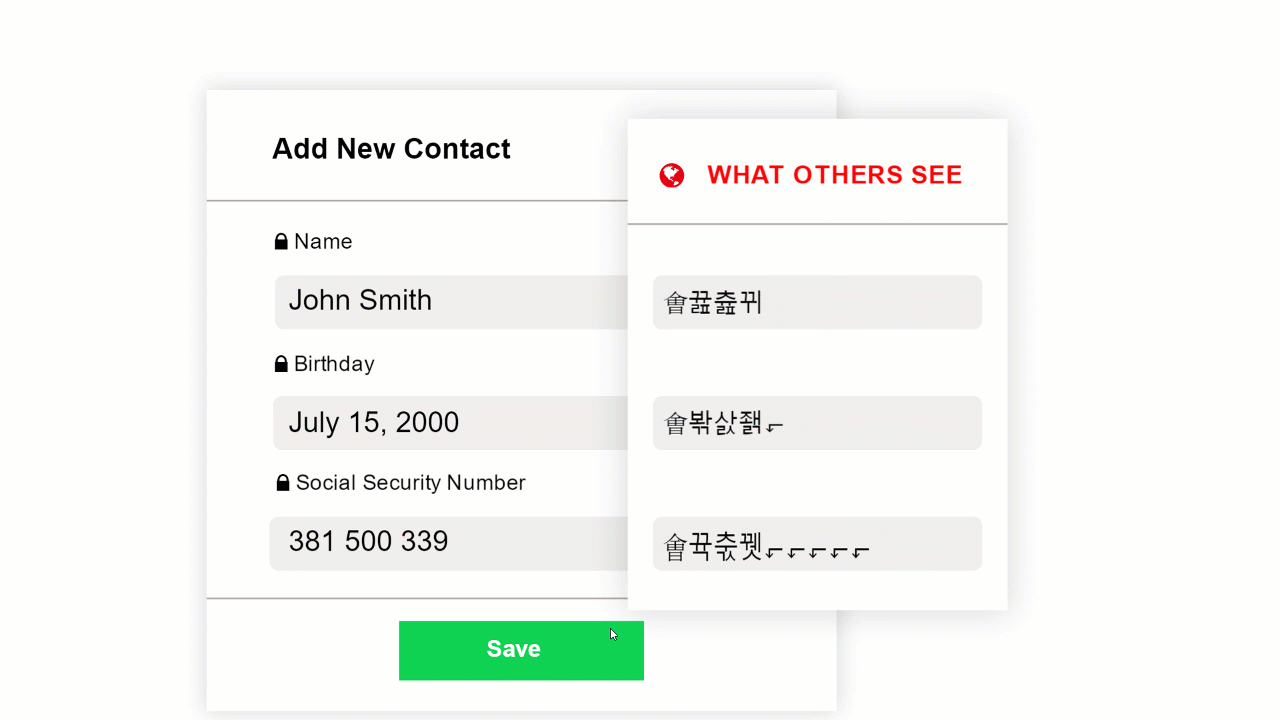
With CloudMask, only your authorized parties can decrypt and see your data. Not hackers with your valid password, Not Cloud Providers, Not Government Agencies, and Not even CloudMask can see your protected data. Twenty-six government cybersecurity agencies around the world back these claims.
Watch our video and demo at www.vimeo.com/cloudmask
Share this article: