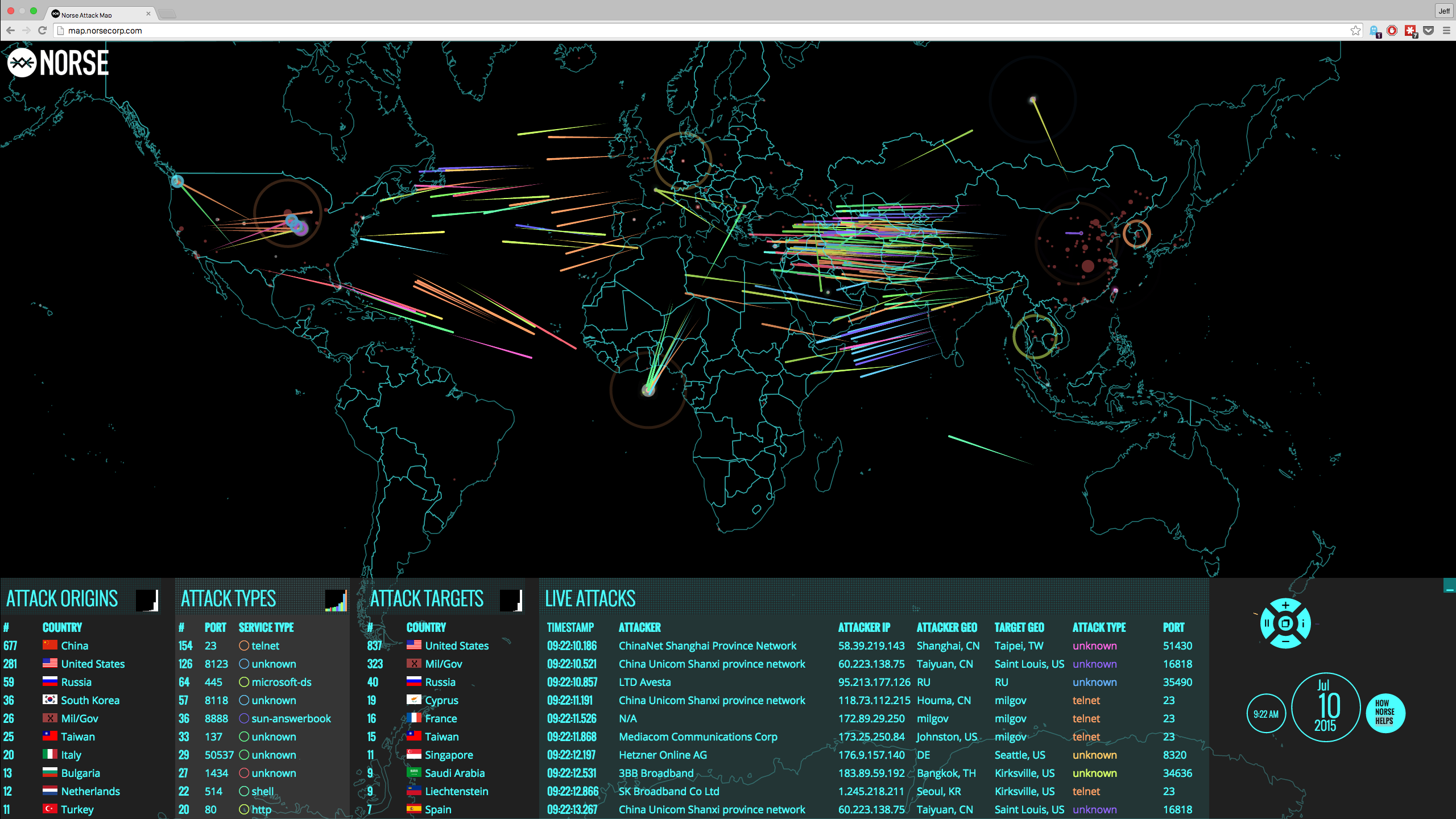
Given the sophisticated nature of modern attack vectors and the value of personal data, it should come as no surprise that criminal organizations have formed with the intent of inspiring political change, committing corporate espionage and instilling their views on digital privacy on the world. In fact, organized cybercrime is a major problem for today's businesses, associations and even public offices, as groups of hackers conspire on the Darknet sharing vulnerability, trading compromised account data and selling new attack vectors.
Marc Goodman, author and global security strategist, explained that stereotypical 1980s hackers - "17-year-old kids living in their parents' basements" - are almost nonexistent, according to CSO Online. Goodman continued, adding that the average cybercriminal is 35 years old, and 80 percent of those black-hat hackers are part of an organized criminal group. This "radical shift"
means that the modern hacker operates "with the professionalism, discipline and structure of legitimate enterprises."
"The modern hacker operates 'with the professionalism, discipline and structure of legitimate enterprises.'"
Jim Anderson, president of Americas for BAE Systems Applied Intelligence, supported Goodman 's statement. The source reported that Anderson claimed there is "no disorganized digital crime. Because of the way criminals have organized, the threat landscape is ever evolving and more importantly, ever growing."
What else about cybercrime has changed?
Business Insider interviewed Hacking Team's CEO David Vincenzetti following the breach that exposed 400GB worth of data, some of which ties Hacking Team to federal governments. Vincenzetti explained that cybercriminals take advantage of the Internet, and sometimes the best way to fight crime is to use similar tools - fight fire with fire. Either way, Vincenzetti admitted that Hacking Team works with numerous governments.
Also indicating the severity of organized cybercrime, WIRED reported that an "underground market for zero-day exploit sales" is certainly real, with at least three critical exploits having been traced back to these sources. One malicious actor - called Starlight-Muhlen - was priced at $100,000, proving that organized groups of hackers have quite the purse.
What's the solution?
The best choice of action for businesses would be to protect corporate data itself, rather than investing in the systems around it. CloudMask does exactly that, focusing on data protection instead of constructing a wall around it. Even with tools to circumvent firewalls, CloudMask keeps data encrypted, safe and away from peering eyes.

With CloudMask, only your authorized parties can decrypt and see your data. Not hackers with your valid password, Not Cloud Providers, Not Government Agencies, and Not even CloudMask can see your protected data. Twenty-six government cybersecurity agencies around the world back these claims.
Watch our video and demo at www.vimeo.com/cloudmask
Share this article: