This is the third part of 5 parts discussion where I will present the main risks of Cloud Computing and how CloudMask addresses those risks. I hope to receive your comments. W.A.
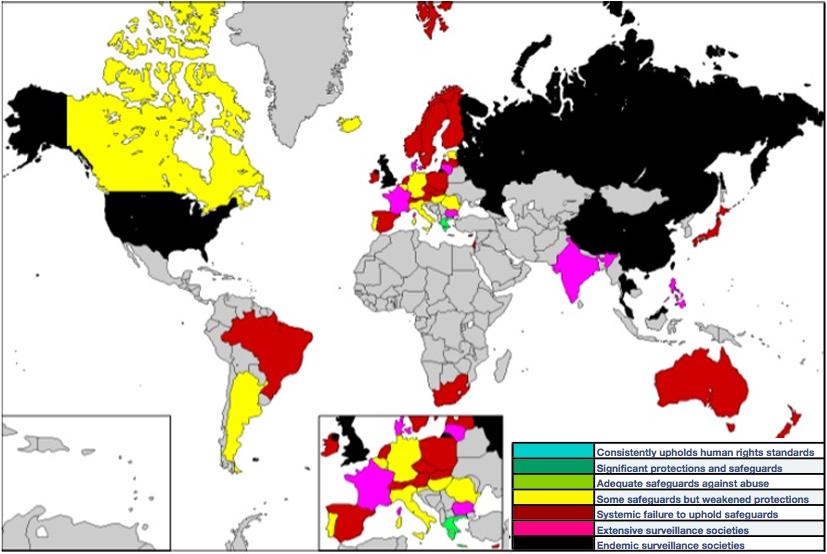
Governments around the world have Digital Surveillance Programs that can be used to demand legal access to your data stored with a Cloud Service Provider (CSP) or Telecommunication companies. Instances of such subpoena are increasing as public security challenges mount (read more in Snowden Digital Surveillance Archive).
Now, CSPs and Telecom companies are regularly publishing reports on Government requests to surrender customers information (Google, Microsoft, Vodafone, AT&T) Owners of the data were not informed that their data had been provided to the authorities. In many cases, the government prohibits CSPs from telling their customers that their data had been handed over.
If we take US government just as an example, it has launched the PRISM and MUSCULAR programs under which the National Security Agency, (NSA) has received broad powers to data mine email and other electronic correspondence.
PRISM and MUSCULAR work under various legal provisions that allow a number of government agencies access to Digital Data. CSPs have to comply with the demands of email archives and user data under various US laws such as the PATRIOT Act and the 1986 Electronic Communications Privacy Act. Under the provisions of the latter, just a mere subpoena is required to demand email 180 days or more old. Many US Agencies such as the FBI and the IRS hold the view that email privacy is not guaranteed by the US Constitution’s Fourth Amendment.
In the second half of 2014, Microsoft has reported that it received more than 31,000 demands for data from various law enforcement agencies. These requests pertained to 52,997 individual cases. Besides, Vodafone’s Law Enforcement Disclosure report (Feb 2015) seeks to highlight some of the most important legal powers available to government agencies and authorities seeking to access customer communications across 29 countries of operation covered in that report. The report says, "few people are aware of these powers or understand the extent to which they enable agencies and authorities to compel operators to provide assistance of this nature."
“We continue to see that a majority of the law enforcement demands we receive come from a handful of countries, led by the U.S., Turkey, Germany, France, and the United Kingdom”. Microsoft, Report on Issues
It is important to recognize that the power to demand access to data is not limited to the facilities that operate in the country where the law applies, but it extends to any facility worldwide owned by a national CSP under the jurisdiction of that law.
In most conventional formats of data encryption, if you are encrypting your data in-transit and in storage, your CSP must have the encryption key so they can decrypt the data before processing and re-encrypt it after processing and before storage or retransmit it to you. In this case, the CSP must surrender your key to the authorities.
CloudMask follows a persistent encryption philosophy. When your data travels out of your end device, it gets encrypted and stays that way. You are the only one that has unencrypted access to your data (see how CloudMask handles encryption). Even if the CSP is forced to hand over your data, it can only give up encrypted data since it has no means to decrypt it.
If you are the only one that holds the key to decrypt your data, you will have to be informed if agencies wish to access your data. In such a situation, you will have an opportunity to raise queries and take legal steps to protect your data and your clients. Thus, CloudMask encryption works as a tripwire to alert you if access to your data is being demanded by government agencies.
CloudMask’s capabilities of encrypting data while it is in use allow you to -
- Encrypt your data before it exits your end device. It keeps the data encrypted even while it is being processed and is under storage in the cloud.
- Maintain complete control over your data because your encryption key is under your exclusive control and your data gets encrypted on your end device.
- Have complete control over your cloud-based email ensuring your emails, attachments, drafts and subject lines are secured - in storage, transit and while in use.
- Ensure that your applications continue to work as before in spite of persistent encryption. All features such as search, listing, sorting, etc. will all continue to function. This can never happen if you are using standard encryption

With CloudMask, only your authorized parties can decrypt and see your data. Not hackers with your valid password, Not Cloud Providers, Not Government Agencies, and Not even CloudMask can see your protected data. Twenty-six government cybersecurity agencies around the world back these claims.
Watch our video and demo at www.vimeo.com/cloudmask







