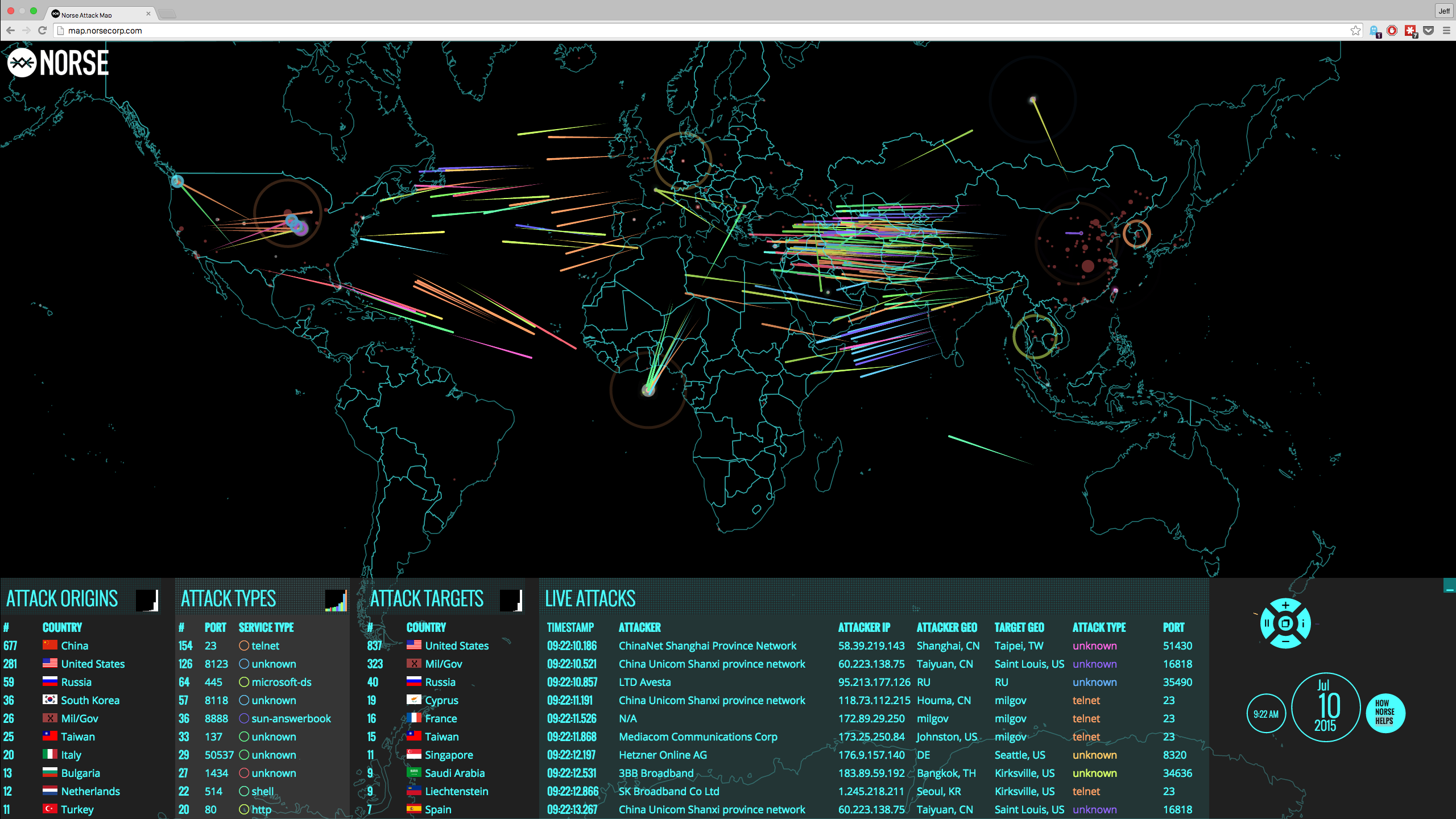
Data breach madness has reached a peak, as organizations slowly but surely discover one by one how no one is safe in today's cyberclimate. And experts universally agree that intrusions are inevitable, since attack vectors keep appearing in the form of systemic vulnerabilities, social engineering and sophisticated malware.
As a result of the growing fear of data breach attempts and their expected outcomes, it is common for organizations to create incident response plans as well as deploy tools that notify IT teams if network activity seems strange. So, modern cybersecurity approaches are ones based on the fact that no one can be trusted and therefore breaches are imminent. This has caused incident report programs to skyrocket in popularity.
However, if IRPs are mandatory to prepare for post-breach circumstances, organizations need to ask themselves these three questions:
1. Will data breaches be discovered?
Verizon's "2015 Data Breach Investigation Report" noted that cyberthreats continue to become more sophisticated and harder to track down. Simply put, if these attacks still stump cybersecurity solutions and make their way past firewall as well as cutting-edge technologies, there is no guarantee that an organization will even know that it's breached, essentially making IRPs useless in the long run.
"Many times businesses will have no idea that networks are compromised."
In fact, Bev Robb, IT consultant, explained to Dell Power More that it's common for businesses to have no idea that data was stolen or that networks are compromised.
"Many times the Darkweb will discover vulnerabilities, exploit/extract the data and share or sell the stolen data before anyone outside of the Darkweb is aware that a breach has occurred," Robb asserted, according to the source.
2. Will tech teams respond in time?
If a hackers or malware are on corporate networks, Verizon explained that IT teams can find them and eradicate them, but that happens far too long after the initial compromise. At that point, it's simply too late. Organizations nowadays just don't have the tools or talent to unearth data breaches before the data is actually stolen.
3. What about internal threats, cloud service providers and government surveillance programs?
While hacktivists and malicious hacking groups certainly pose a large threat to corporate data security and personal data protection, internal threats are still largely responsible for data breaches. As a recent example, Business Insider reported that the CEO of Avid Life Media - the parent company to Ashley Madison - Noel Biderman stated that the hacker was "definitely" someone with access to the organization's internal tech services.
Furthermore, how will organizations know if their third-party service providers (TSPs) were breached? After all, businesses own internal IT teams can find a data breach, so no one should expect TSPs to be any better at discovering sophisticated threats. And then there are government surveillance programs to worry about nowadays, as some public officials have made it clear that they deserve access to sensitive corporate data. If cybercriminals use cutting-edge tactics, organizations should consider what the government is capable of doing.
NIST “Security Incident Handling Guide” report, stated “An incident response capability is necessary for rapidly detecting incidents, minimizing loss and destruction, mitigating the weaknesses that were exploited, and restoring IT services.” All are reactive measurements; none is proactive data protection.
Simply put, IRPs won't change the fact that any these individuals can easily access unencrypted data.
The CloudMask solution
Organizations need to protect data itself, not access to that data. By tokenizing information, data is protected not only when it moves on the network and at rest, but when using that information for work purposes. CloudMask and tokenization mean that no one can see data, hackers or employees - expect for the owner or explicitly approved parties.

With CloudMask, only your authorized parties can decrypt and see your data. Not hackers with your valid password, Not Cloud Providers, Not Government Agencies, and Not even CloudMask can see your protected data. Twenty-six government cybersecurity agencies around the world back these claims.
Watch our video and demo at www.vimeo.com/cloudmask
Share this article: