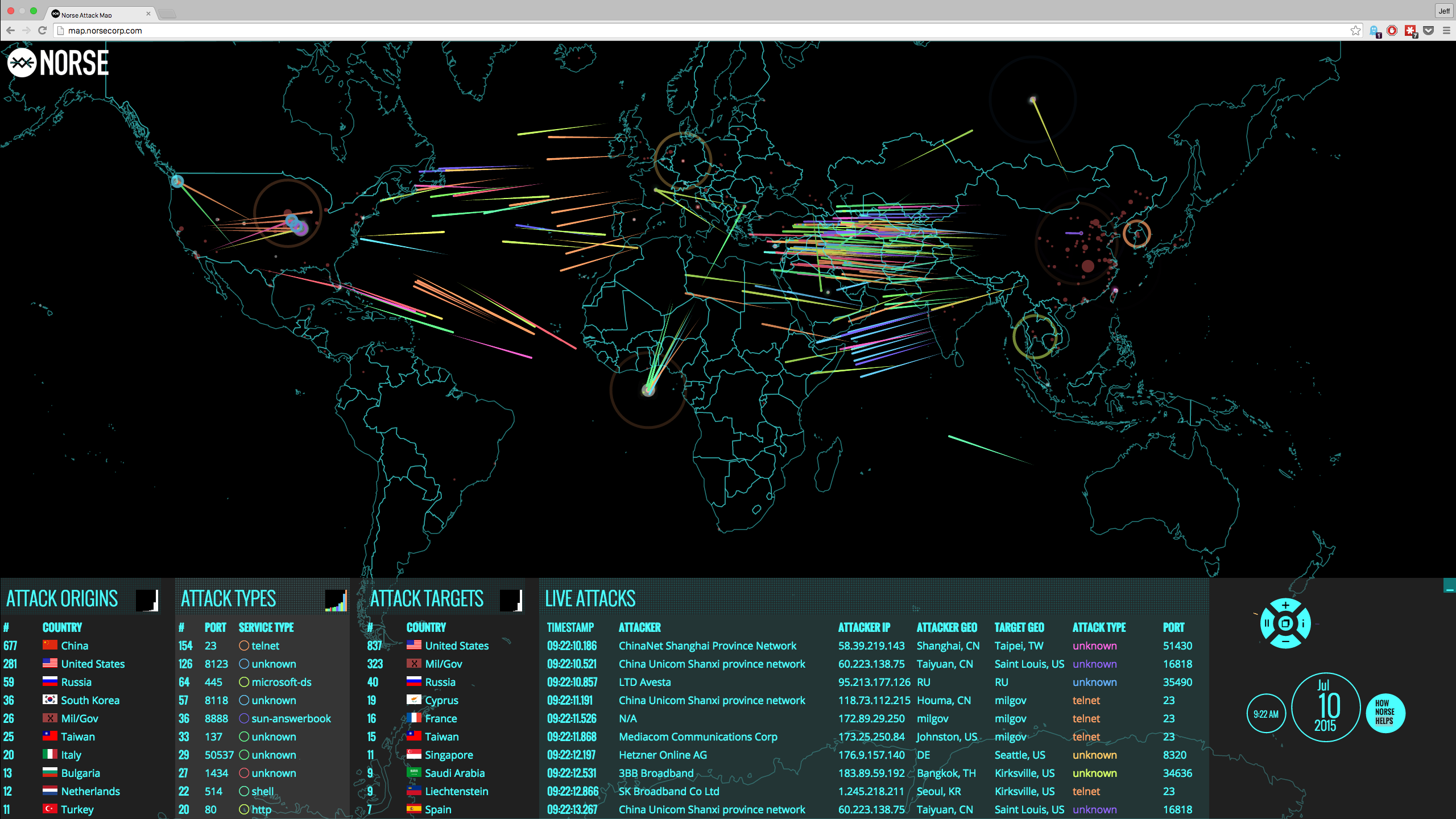
This article is the second of a series that explores data breach risks and issues related to regulatory compliance, associated costs and loss of reputation. In “Threats and Consequences” we look at the types of cyber threats and what the consequences might be for businesses that suffer data breaches. As described in the first article of the series, “What You Need to Know
This article is the first of a series that explores data breach issues, threats to data security, compliance with regulations and effective solutions to reduce the risk of data breaches. In "What You Need to Know” we define key terms and provide an overview of the data security problems businesses are facing. Data breaches are becoming more frequent while government...
Data manipulation could mean disaster for corporations, health care providers, national security agencies and individuals around the world. Businesses and consumers both invest time and money into securing private information, but too often, the focus is on preventing hackers from accessing data and therefore ensuring that sensitive information, trade secrets and...
Reports of data protection fails against insiders, compromised cybersecurity and data breaches are becoming more frequent, even at large corporations and the government. But these events are not all the same. You can analyze them and, by classifying the data breaches based on how they happened, you can develop effective countermeasures. One way data breaches occur is...
If you work in the law profession or are an IT professional responsible for law firm records, you know to what extent your business depends on the ability to keep sensitive client information confidential. The issues raised by storing law firm client data digitally are data security, data accessibility and the maintaining of legal privilege. When you store client...
Effective cybersecurity is essential for law firm operations, for regulatory compliance and for keeping a good reputation, but it requires a familiarity with the principles of secure IT. Legal ethics require that lawyers keep private information secure and preserve client records. As a member of the legal profession, you have to ask how service providers deal with...
Data Masking as a Solution to Password Weaknesses Password-based data protection is the most common form of data protection, but it is increasingly weak. If you think your data is secure because your organization insists on strong passwords, you are increasingly likely to be wrong. Better software tools running on powerful processors can try millions of character...
February 09, 2017
Leave a comment
New Security Paradigm,
Breach,
Password,
Data Masking,
data privacy,
cyber threats
By CloudMask Team
February 3, 2017, US Magistrate Judge Thomas Rueter ruled that Google must provide emails stored overseas to US authorities for domestic investigations. On August 2016, courts issued two search warrants, which required Google to disclose, to the FBI, electronic data held in the accounts of the two accused of fraud in violation of federal law. Google only provided data...
What Is Wrong With Passwords-based data protection? Today, Password-based data protection is the foundation of 99% of data protection. It’s ubiquitous: you want access to an account or information, so you type your username and password, and you can get in. For critical and restricted information, you might have to do it again, with a different password. Your company’s...
February 06, 2017
Leave a comment
Password,
Data Masking,
data privacy,
cyber threats
By CloudMask Team
Over the years, Google has emerged as the world’s largest collaboration and business use platform. It has nearly a billion subscribers and a complete application ecosystem that comprises email, file storage, calendar, office applications and business collaboration capabilities. Most of these services can give small and medium businesses capabilities that match those...
February 03, 2017
Leave a comment
Google,
Password,
Data Masking,
Government surveillance,
cyber threats
By CloudMask Press