 By Joseph Steinberg CEO, SecureMySocial @JosephSteinberg
By Joseph Steinberg CEO, SecureMySocial @JosephSteinberg
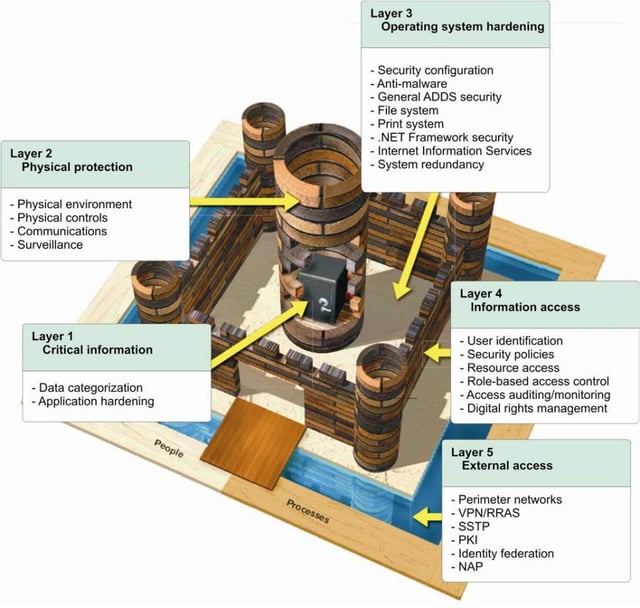
For many years, information security professionals have discussed, and promoted, a strategy known as “Defense In Depth,” in which an organization utilizes multiple layers of security controls rather than just one layer, with the hope that if some vulnerability exists in one of the layers, the countermeasures in one or more of the other layers will compensate for the deficiencies, and deliver the necessary security. Furthermore, utilizing a proper implementation of Defense In Depth can increase the time that it takes a hacker to penetrate an organization – which also increases the chances of stopping him or her before he or she is able to steal data or commit other harmful acts. Sometimes Defense in Depth is known as layering, or as utilizing the “Castle Approach,” named for the physical security strategy employed by the builders of many of the castles of yesteryear by which multiple physical layered defenses were utilized to prevent breaches of the structures by invaders.
There is, however, a fundamental flaw in many Defense In Depth implementations: Often, multiple technologies are added to address the same risks, while other dangers remain effectively ignored. When one considers that one of the primary goals of info-security controls is to protect information, this phenomenon translates into situations in which Defense In Depth implementations leave information that needs to be protected vulnerable to compromise.
Consider, for example, internal risks – which are, of course, normally more dangerous than external risks. An employee gone rogue, for example, may know which organizational data is most valuable and where and how it is stored – technology layers that combat only external risks will do nothing to prevent that individual from pilfering information and inflicting serious harm. Layering firewalls, intrusion detection systems, and many other network security tools will not reduce the exposure to the risk posed by an insider – and adding more and more layers that address similar risks will not make the situation any better. Reinforcing the strong parts of a dam does not do much if there is a hole in the structure.
Even protecting databases and other data storage repositories will do little to protect against risks that involve people who have access to those stores. Likewise, if you store and process data in the cloud, you are at risk from not only outsiders, but also from the cloud provider itself – and that provider likely has access to your data storage systems. Similar to the case of rogue employee discussed above, if you do not protect your data via encryption et. al. someone working at the cloud provider could potentially access and pilfer your data – layering security technologies will not stop the theft if some of the layers do not address the data risks.
So what do you need to do in order to layer properly?
Consider what it is that you really want to protect, understand the risks to that asset, and protect accordingly.
In the case of information security, data is the asset, so you must maintain an information-centric mindset when crafting, implementing, and testing a Defense in Depth strategy.
Sensitive data needs to be secured during its entire lifetime wherever it resides.
When you design the “layers” consider how automakers design the safety elements of cars: in the end, all of them serve one goal – to protect humans from injury or death. The focus of car designers is not on creating better anti-lock brakes for the sake of making braking better, for example, it is to lower the number of collisions and reduce the severity of collisions that do occur. Each automobile safety feature offers its unique shielding capabilities for the true asset, the people in the vehicle. Information security should follow a similar model – each technology deployed or policy implemented should serve the primary purpose of protecting the data, with some trying to stop breaches and others trying to reduce the severity of danger when a breach occurs.
Keep in mind that because people and systems need to access data in order to function, layering network and application level technologies that simply block access altogether is infeasible and impractical; hence, encryption, hashing, tokenization, data masking, and other direct information-protection techniques are often useful when layering. Furthermore, whenever possible, restrict sensitive data to as small as possible a number of systems and networks – and focus security budgets disproportionally on protecting what matters most.
Share this article: